I started by installing the APK on an android phone, once opened it will show a text field to enter a key and a login button, the APK will try to navigate to https://you-shall-not-pass when trying to type any key (maybe this was done to prevent bruteforcing the key?), finally, when you try to login with a random key It will show a dialog saying “BAAAD Key”
I dropped the APK within jadx and I went to the entry point which is com.expor4bb1t.AwesomeProject.MainActivity, I could see a lot of imports related to facebook and react, which along with the challenge name, started making sense. This application is built with react native.
It turns out that react native applications basically can run java script code that is located in assets/index.android.bundle
However, in our case, the javascript code was compiled into what is called “Hermes Bytecode”, which is run by a custom javascript engine.
This bytecode makes the application faster but is gibberesh to humans, this is why we have to either disassemble it into readable hermes assembly, or even better, we can decompile it into javascript.
I found https://github.com/bongtrop/hbctool which is a disassembler for the hermes bytecode, however It didn’t work for me as It only supports up to version 85 of the bytecode, and our apk seems to be version 94 so the tool errors out.
PS C:\Users\hegzp\Downloads\ReactiveVaultStuff\assets> hbctool disasm .\index.android.bundle out.hasm
[*] Disassemble '.\index.android.bundle' to 'out.hasm' path
Traceback (most recent call last):
...
<snip>
...
AssertionError: The HBC version (94) is not supported.
I found this writeup where that author faced a similar problem, and apparently, adding support for newer versions shouldn’t be that hard, but I decided to dig a little more and I found this repo, It is basically a decompiler for hermes and they even support our bytecode version.
I ran the tool on the index.android.bundle using hbc-decompiler.exe .\index.android.bundle out.js to get a decompilation of the bytecode.
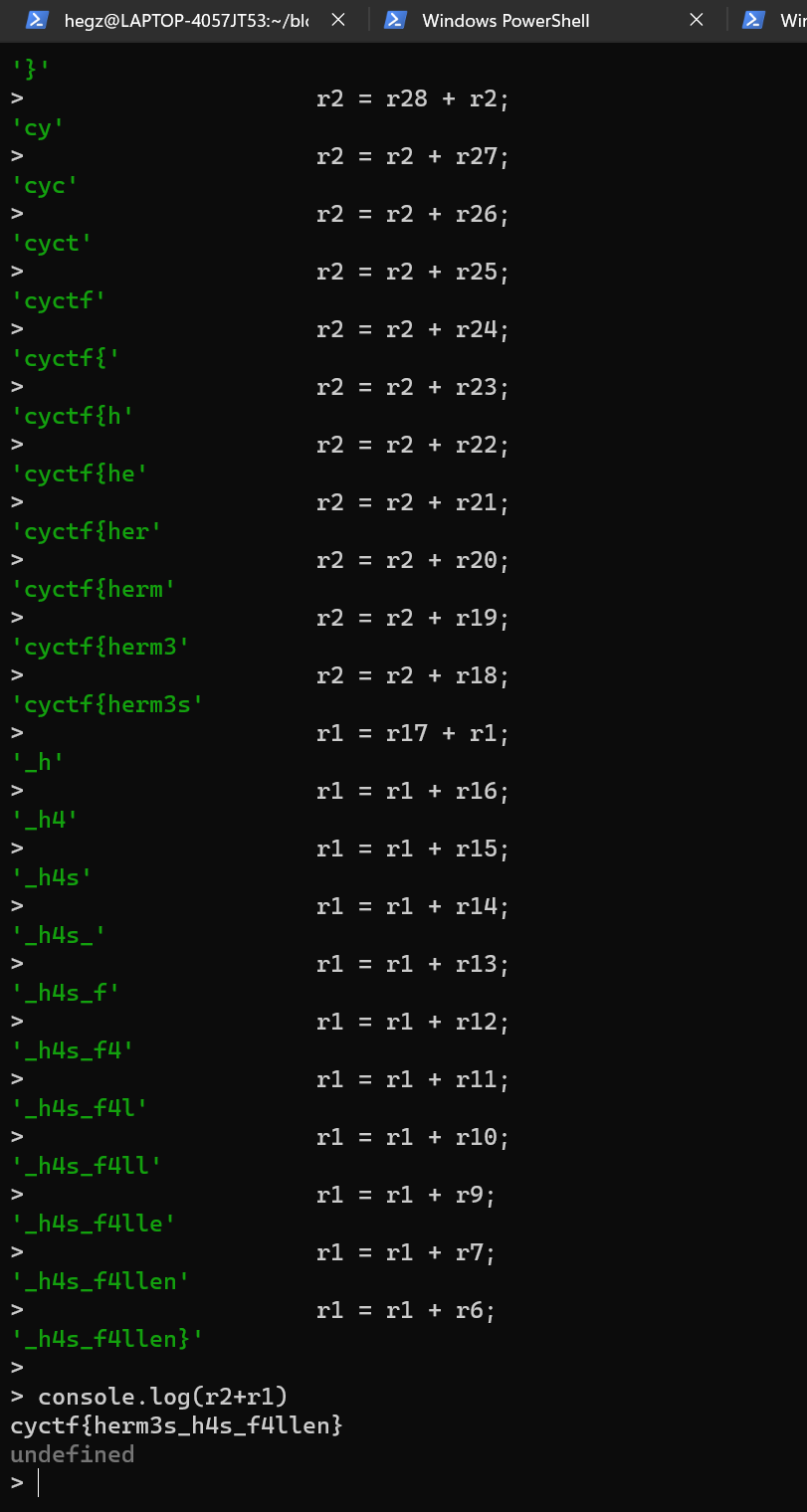
Once I found this decompiled code, I did a search for the BAAAD Key string that we saw in the APK earlier, and I found one result.
| |
This seems to be some sort of switch logic for the login button, I did some more digging then I found this suspicious piece of code, It was just above the login switch logic that we discussed in the above paragrarph.
| |
I could recognize this immediatly as some sort of dynamic string construction, so I just threw it in a js repl.